Introduction
Microsoft introduced “Cloud App Discovery” more than a year ago, but not many enterprises benefit or even thought about using this service.
It’s actually very simple, Microsoft explains this very good in its own words:
In modern enterprises, administrators are often not aware of all the SaaS applications that are used by the users to do their work. As a consequence of this, administrators often have concerns in conjunction with unauthorized access to corporate data, possible data leakage and other security risks inherent in the applications. Because they don’t know how many or which apps are used, even getting started building a plan to deal with these risks seems to be daunting.
Benefit
So, what can you expect form this:
- discover applications in use and measure usage by:
o volume (traffic)
o number of users
o number of web requests
- identify the users that are using an application
- export data
- easier to practice shadow IT
- bring applications under IT control and integrate applications easily to enable
o single sign-on
o user management
What do you need
Cloud App Discovery is part of the Azure AD premium features portfolio of Microsoft.
With the new licenses models of Microsoft, a P1 license is sufficient.
Keep in mind that only the admins that want to access the logs and reports need a license, so you’re users don’t need any kind of license for this, this is the nice part of the service.
There is not much needed to configure it’s an out-of-the box service.
Follow these few steps and you’re good to go:
1) Login to your Azure portal as an Administrator (https://portal.azure.com)
2) Search for “cloud app discovery”
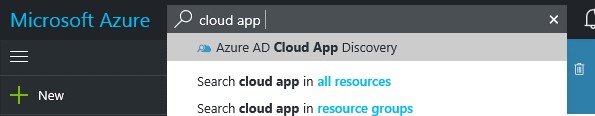
3) Click on “create” and you can start configuring it.
4) Go to settings
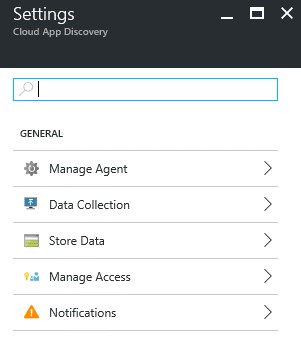
For the Agent part, you only have a few options that can be changed.
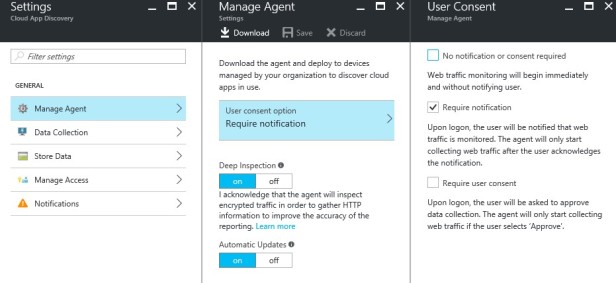
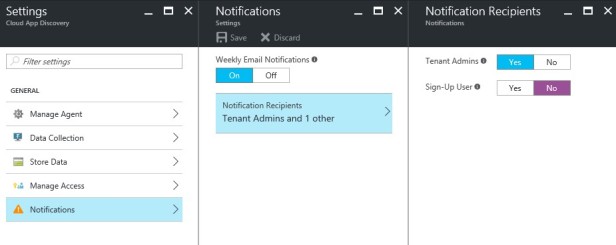
Notification for the users is the most important part, this is can be a legal issue if you don’t configure it correctly.
Deep Inspection and Automatic Updates can be set/left to “on” nothing special about these things.
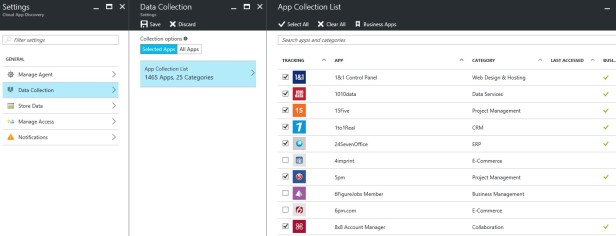
On the data collection part, you can select which apps that can be discovered. There are about 1465 apps and 25 categories.
If you want to use the data for your own research, this is possible in the “store data” section.
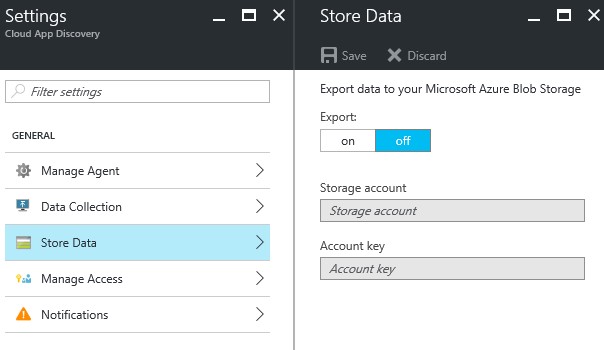
You can export the data to Azure Blob Storage if you want using the configuration screen above.
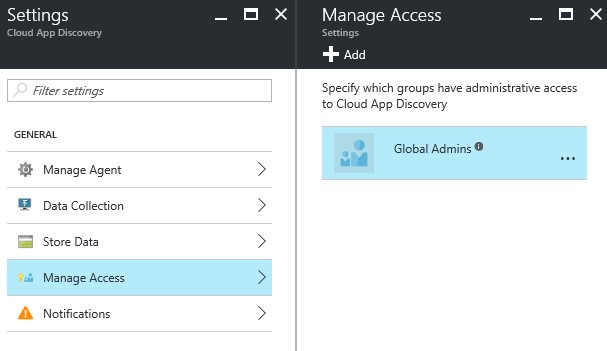
Through Manage access, you can add people that can use this service and consult the reporting and/or settings.
Notifications can be set in the last menu item. You don’t have many options here, only on weekly base.
Once you have checked and changed the config, we can start using the service.
How does it work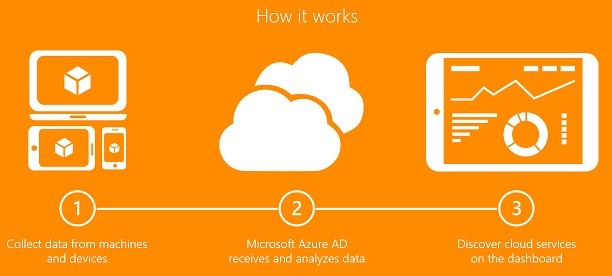
Collecting data
With cloud app discovery, the data retrieval part is accomplished by agents that run on computers in your environments.
You need to deploy a client agent to the machines/users you want to assess.
This is done using the client that can be downloaded in the portal:
You can also deploy the client using GPO’s or SCCM for large scale deployment:
After installation, you’ll see this in your services:

Uploading data
The app usage information that is captured by the agents is send over a secure, encrypted channel to the cloud app discovery service on the Azure platform.
Analysis
The cloud app discovery service evaluates the data and generates reports you can use to analyse your environment.
You have a few basic reports available on the portal.
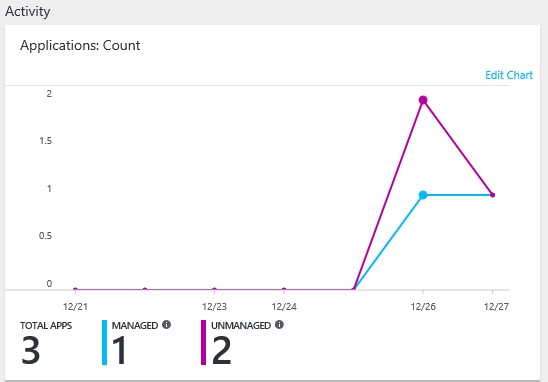
- The total number (count) of observed apps, the number of unmanaged apps and the number of managed apps. This graph can be modified to show volume or web requests.
- The total number of observed users.
- The total number of observed agent installations.
If you go to the details, you get the list of managed and unmanaged applications.
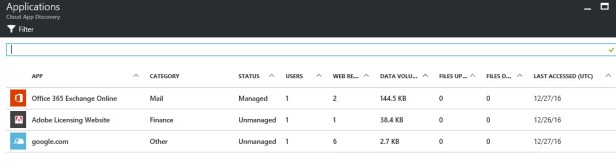
You can do the same for “users” and “agents”.
Disadvantages
The only disadvantage is the agent that is needed for the assessment:
- Agent is an executable, not an MSI package
- Agent is not fail proof with other clients (for example with the Microsoft TMG agent)
Conclusion
Very nice service, can be setup very fast without a lot of additional work (except client deployment).
Data from this tool is also being used for the Azure AD Identity Protection service that Microsoft released a few months ago.