Last week my colleague Jasper Bernaers embarked on a mission to explain what an Identity is and why it’s important. You can find his post here. The cloud is more and more a common platform including cloud services like O365. If that one Identity is that important, we need to make sure that you know who has access to that account.
But not only a central managed Identity is important. What apps are being used with that account or device? Christophe Lambrecht showed us a tool which can help detecting applications in your environment. Read about it here: Azure AD: Cloud App Discovery
Let’s connect the dots: why not analyze this? Security is hard enough as it is and we have to make sure that the end user still can work easily.
What is Advanced Threat Analytics?
We need to create visibility in how your users work, what is normal behavior,… ATA detects multiple suspicious activities, focusing on requests made to the Active Directory:
- Reconnaissance: the gathering of information on how the environment is built, what are the different assets and entities which exist. Attackers are generally building a plan for the next phases of the attack.
- Lateral movement cycle: spreading their attack surface inside your network.
- Domain dominance (persistence): capturing the information allowing them to resume their campaign using a various set of entry points, credentials and/or techniques.
These phases of such a cyber attack are similar and predictable; no matter what type of company is under attack or what type of information is being targeted. ATA searches for three main types of attacks: Malicious attacks, abnormal behavior and security issues.
Malicious attacks are detected deterministically, by looking for the full list of known attack types including:
- Pass-the-Ticket (PtT)
- Pass-the-Hash (PtH)
- Overpass-the-Hash
- Forged PAC (MS14-068)
- Golden Ticket
- Malicious replications
- Reconnaissance
- Brute Force
- Remote execution
How can I test ATA?
A test lab that simulates a basic setup of a single domain is enough to get started. ATA will capture packets via port mirroring or a lightweight agent.
Get a copy at Microsoft Advanced Threat Analytics.
You need at least 4 machines not considering the VM Host:
- Domain controller
- ATA Center
- ATA Gateway
- Client to generate logins and suspicious activity
The server OS used is 2012r2 with .NET framework 4.6.1 and the client is Windows 10 Enterprise. Finally, create a Read user for ATA. A normal domain user is sufficient.
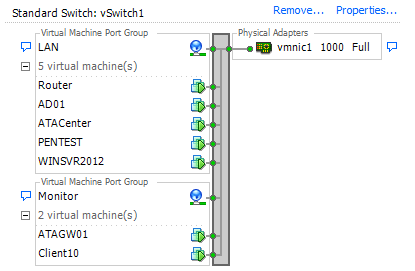
The gateway needs 2 NIC’s where 1 will function as capturing device. We want all the traffic from and to AD01 VM mirrored to the second vice of the receiver Gateway. Other VMs do not need all this traffic. Using standard switches, the only solution is in VMWare by adding a port group on the vSwitch:
Installation and configuration
I’ll quickly run through the installation process. Mount the ISO and start the setup. Choose a language and accept the license agreement. I enabled ATA updates so new threats can be detected:

The database will be located on a different path when installing in production.

- Center service IP: this is the IP where the gateways will connect to.
- Console IP Address: this is the IIS server and user console.
- Here you can generate a self-signed certificate or upload a certificate.
After pressing launch, ATA will open the console to make the first configuration changes. You can log in with the user used for the installation.
Add the read user:
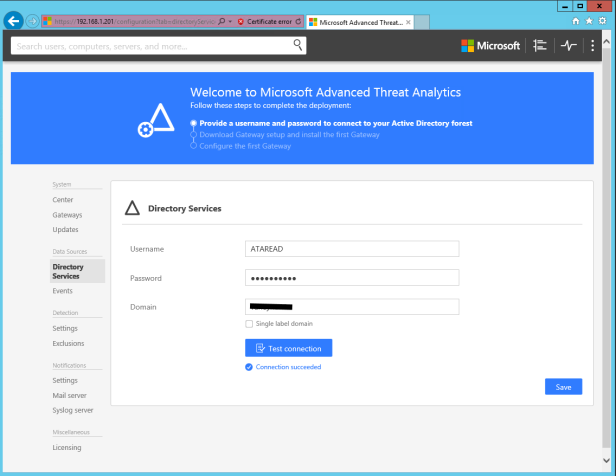
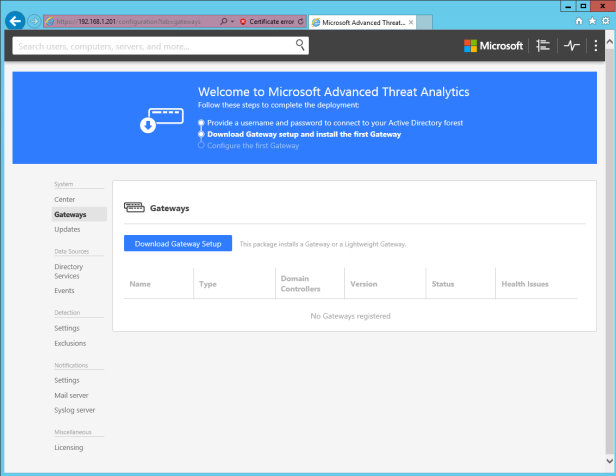
At this point, we can start adding gateways to capture the data. Download the zip and copy it to the gateway server. If copied to an AD it will choose to install the lightweight agent.
The gateway agent will ask to enter a user. This user must be a member of the Advanced threat analytics administrators.
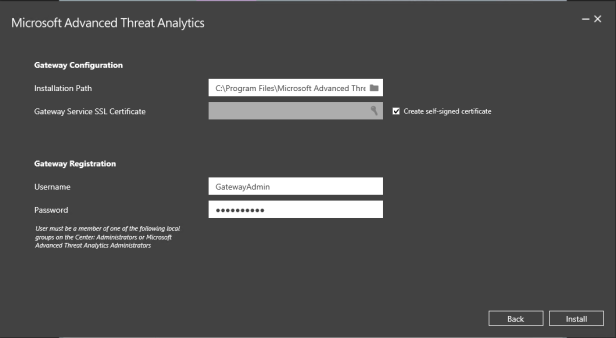
This will add the agent to the ATA centre:
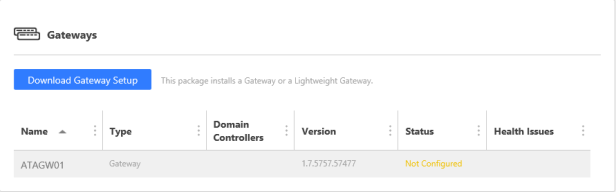
Now we link it to the AD to start the capturing:
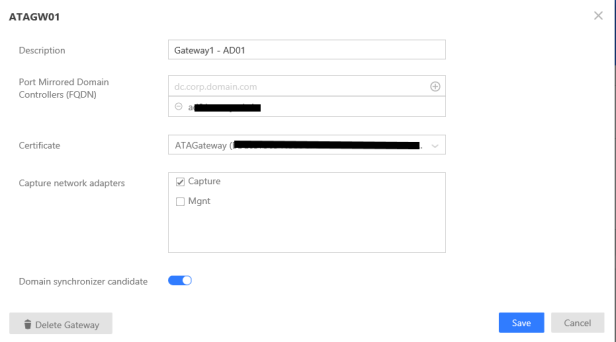
How my login can be abused?
Now that the analytics can read all the authentication request it will start learning abnormal logins or actions. Basic attacks will start with reconnaissance and if an admin isn’t careful with his account this can easily be exploited.
So I tested how ATA detects this.
Sensitive Account Credentials Exposed
In this example an exploit makes the admin enter his credentials over an insecure connection like LDAP bind or HTTP.
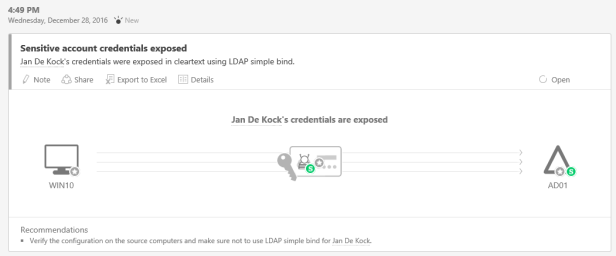
ATA will recognize this and generates an incident with a recommendation.
Reconnaissance using DNS
Attackers will start with creating a sort of topology of your infrastructure and network. DNS is an easy target. DNS information for the target network is often very useful reconnaissance information. DNS information is publicly available information and enumerating it from DNS servers does not require any contact with the target and will not tip off the target company to any activities.
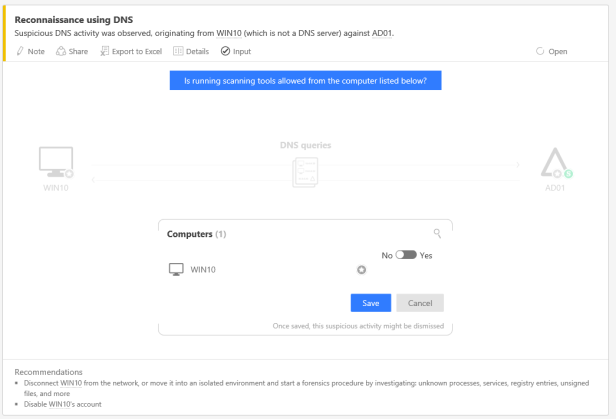
Here you notice the learning curve for ATA, you can specify that this is normal application behavior. Otherwise, it’s best to follow the recommendations.
Remote execution attempt
After that an attacker has enough information and a compromised account, they’ll probably try to increase their grip on the platform. Executing programs remotely to gain access or additional info is most likely the next step.
Let’s assume they want a password dump from our AD:
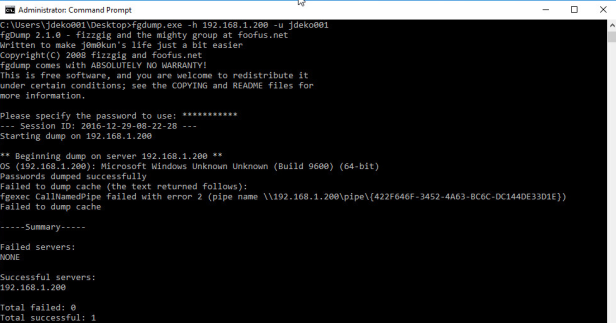
This is seen as remote execution and is flagged by the centre:

Conclusion
Advanced Threat Analytics is a basic first step for learning your environment. The setup doesn’t require a lot of resources and this makes Advance Threat Analytics available for most companies. Adding event log shipping or SIEM (security information and event management) logs will immensely increase how fast it can learn or detect.
ATA as part of the Enterprise Mobility + Security Suite is a very important tool in getting ahead of the attackers. Detect the breach, not the effect of the breach.



Can I simply say what a relief to uncover someone that really understands what they are talking about on the internet. You certainly understand how to bring an issue to light and make it important. More and more people ought to look at this and understand this side of the story. I was surprised you’re not more popular given that you most certainly possess the gift.
LikeLike
Nice blog right here! Additionally your site a lot up fast! What host are you the use of? Can I am getting your associate hyperlink on your host? I wish my web site loaded up as quickly as yours lol
LikeLike
Great article.
LikeLike
Normally I don’t learn post on blogs, but I wish to say that this write-up very compelled me to take a look at and do so! Your writing taste has been amazed me. Thanks, very great article.
LikeLike